What is Polymorphic Encryption?
Securing sensitive data while keeping it usable for real-time operations is a significant challenge. Methods like homomorphic encryption allow computations on encrypted data but the performance isn’t acceptable for real-world applications. Tokenization replaces sensitive data with tokens, but it breaks search, AI, and most operations on data.
With the growing amount of data breaches and increasing number of regulations, businesses demand a system that supports security, performance, and usability. We need a way to keep data encrypted and secure while remaining functional and efficient.
In this article, we discuss polymorphic encryption and polymorphic tokenization, which offers a balance between data use and data security, while also meeting the performance demands of a modern system. To understand polymorphic, let’s first look at homomorphic encryption.
What is Homomorphic Encryption?
Homomorphic encryption is a method that allows computations to be performed directly on encrypted data without needing to decrypt it first. This means you can execute operations like addition and multiplication on encrypted values, and when you decrypt the result, it will be the same as if you had performed the operations on the plain-text data.
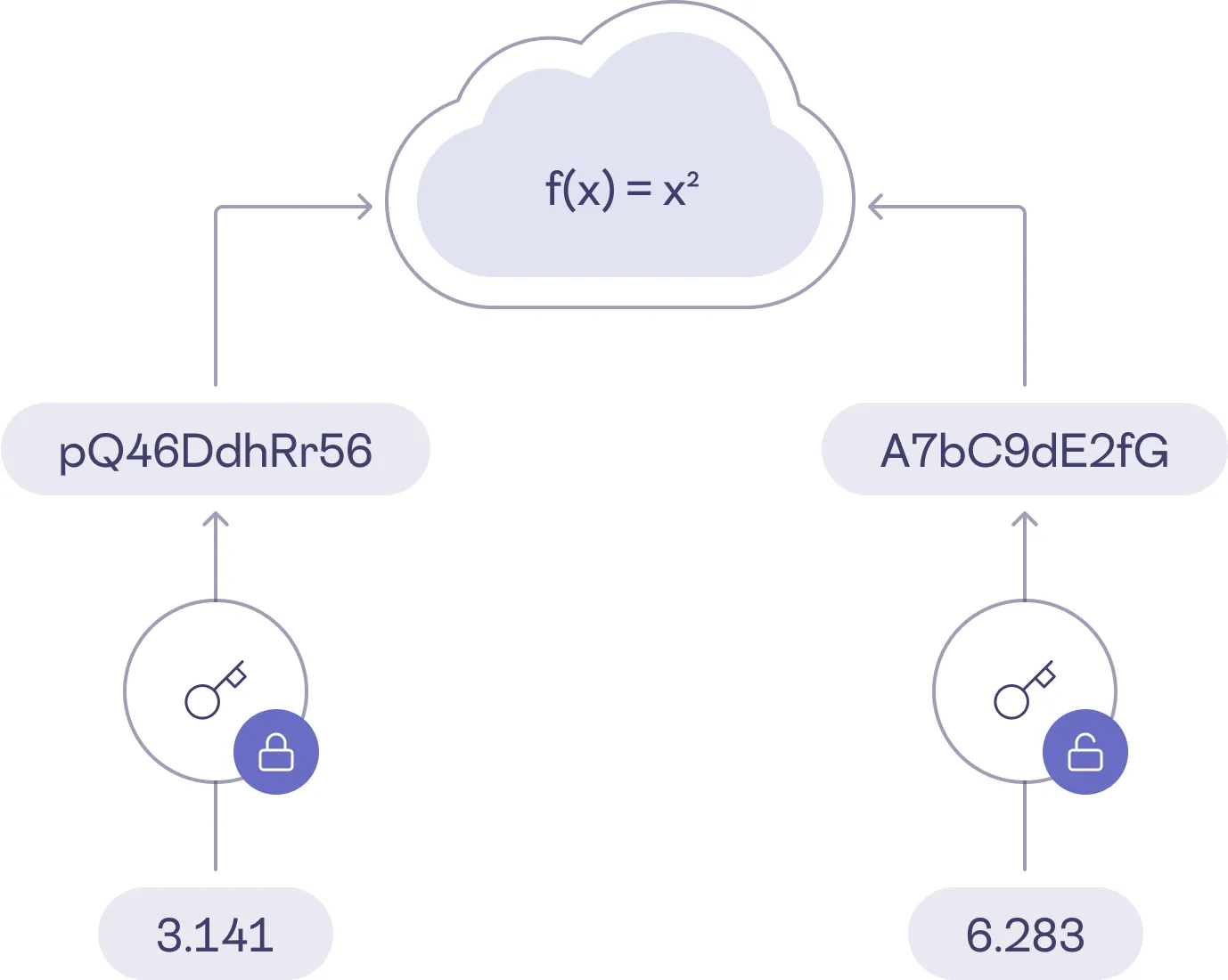
With more sophisticated homomorphic encryption schemes, a wider variety of operations can be executed repeatedly. At first glance, this capability seems to offer a perfect balance between data security and usability.
However, despite its reputation as a "gold standard," it has practical shortcomings that make it not viable for many applications.
One primary issue is the enormous computational power required. Fully homomorphic encryption demands such intensive computing resources that, even with advanced hardware, operations can be prohibitively slow. For instance, Microsoft's documentation on their homomorphic encryption library highlights its inefficiency. The resulting performance bottlenecks make it unsuitable for most business applications due to unacceptable latency.
These performance issues stem from the goal of homomorphic encryption: to support a wide range of operations on encrypted data. In reality, most developers only need to perform a few specific operations on sensitive data.
Consider a scenario where you need to determine a customer's location by matching their encrypted phone number to a database and checking the country or area code. It’s uncommon to need to perform arithmetic operations like multiplication or addition on a customer’s phone number. Therefore, it's not logical to endure slow performance to support such rarely required operations.
The main challenge with homomorphic encryption is its ambitious goal of enabling numerous operations on encrypted data while deciding which operations to support after the encryption process. This broad objective, while theoretically impressive, results in practical inefficiencies that limit its real-world application.
What is Tokenization?
Tokenization provides an alternative approach to data security by replacing sensitive information with non-sensitive tokens. Unlike homomorphic encryption, tokenization doesn't aim to support a wide range of operations on encrypted data, making it a simpler and often more efficient method for protecting sensitive data.
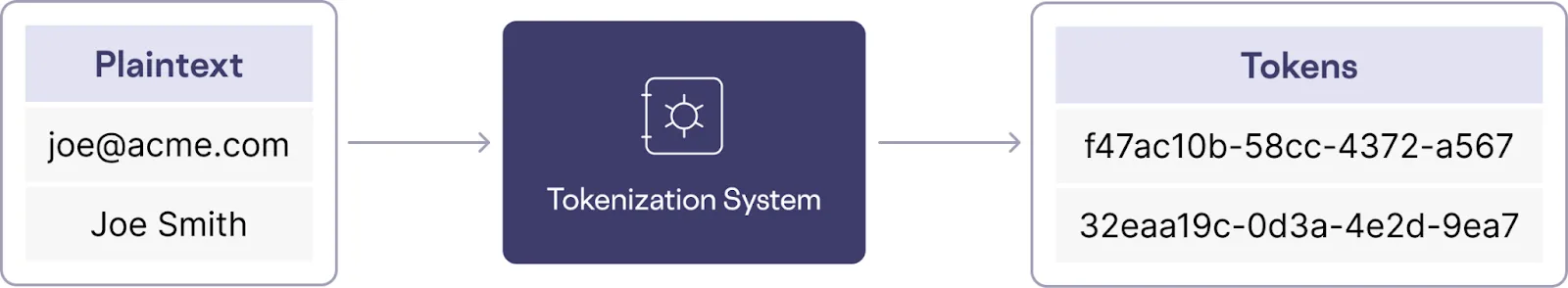
However, tokenization has its limitations.
It disrupts the original data format, making it challenging to perform searches, pattern matching, and other operations directly on the tokenized data. This disruption also affects sorting, filtering, and aggregation since tokens lack the inherent properties of the original data.
APIs and downstream services often have specific expectations about data formats. Tokenized data can break these expectations, leading to integration issues and potential system failures. Additionally, different use cases require different types of tokens. For instance, while tokenizing a credit card number might need to maintain a certain format, a tokenized phone number might need to handle different aspects like the last four digits, area code, or full value.
Detokenization—the process of converting tokens back to their original form—also has these varied requirements. For example, one use case might require retrieving only the last four digits of a phone number, while another might need the area code, and a service like Twilio might require the complete phone number.
Understand when vaultless tokenization falls short. Get the guide →
What is Polymorphic Encryption and Polymorphic Tokenization?
While homomorphic encryption is powerful in theory, it suffers from significant performance issues due to its broad and complex capabilities. Tokenization, on the other hand, simplifies security but breaks search, AI, and most operations against the data.
Skyflow’s patented polymorphic encryption addresses these challenges by incorporating the concept of polymorphism from computer science. With polymorphic encryption, data is encrypted in various forms and with different keys, tailored to specific functions associated with real-world use cases for sensitive data. This approach combines flexibility with robust security, while also being computationally more efficient than homomorphic encryption.
Polymorphic encryption supports operations on partial data. For example, in the image below, the year, country code, and area code can be encrypted in one way to support data analytics, while integrating with Twilio will require the full phone number, and identity verification uses another set of customer data and doesn’t have access to the phone number. Each workflow has the data that it requires, and nothing more. And importantly, none of these workflows has access to all of the sensitive PII for a given customer.
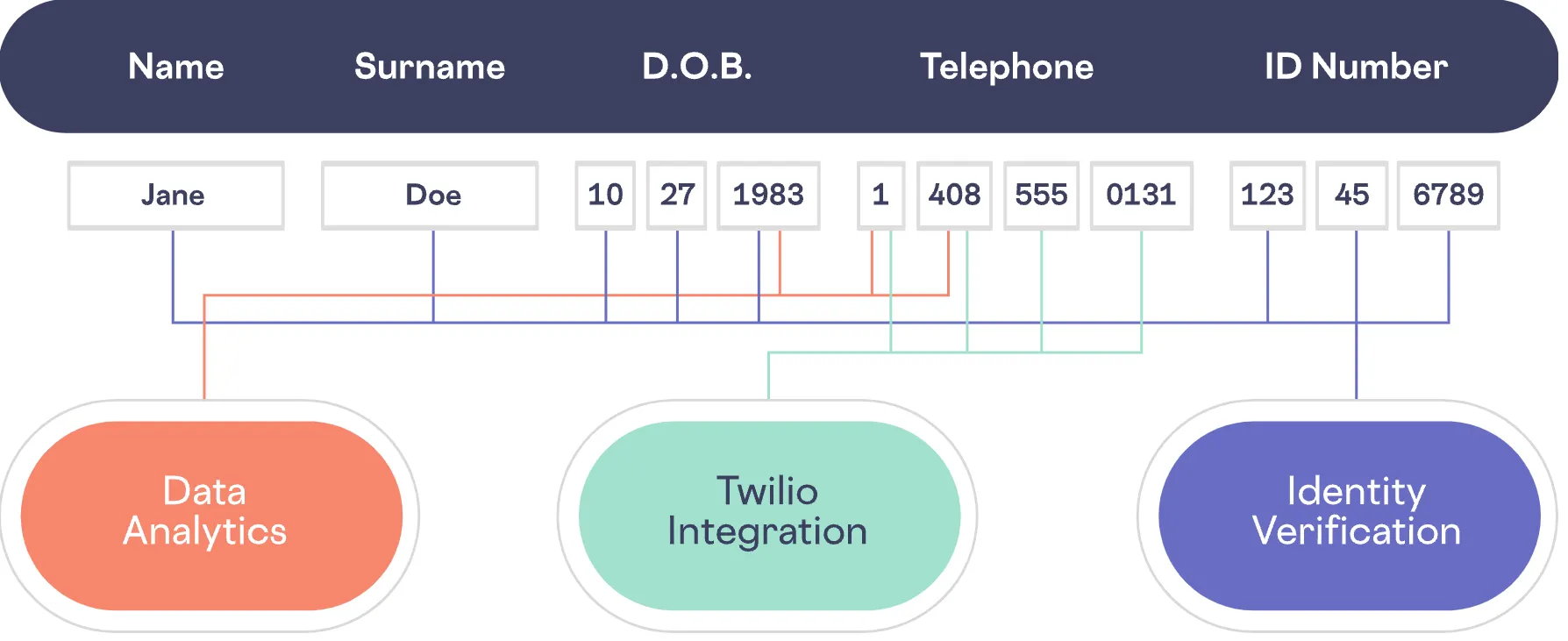
For instance, if you only need to determine a customer’s location using just the area code of a phone number, you don’t need to decrypt the entire record. Since phone numbers are data structures composed of multiple identifiers (such as country code, area code, and local code), polymorphic encryption allows for operations on these partial elements without exposing the full record. This selective data access enhances privacy and security by reducing the need for full data decryption.
Additionally, polymorphic encryption is designed for high performance by supporting only the operations that are known and necessary. By limiting the operational search space to practical uses of the data, this ensures that the system performs efficiently, avoiding the latency issues associated with homomorphic encryption.
Skyflow’s polymorphic tokenization complements this by offering flexible token creation and detokenization tailored to specific use cases. It supports a range of token formats and detokenization methods to meet varied requirements, ensuring that data remains secure while still being functional across different scenarios like search, analytics, and AI.
The polymorphic engine is key to overcoming the limitations of traditional methods, delivering both security and performance in handling sensitive data.
Examples Use Cases of Polymorphic Encryption
Polymorphic encryption offers a flexible and efficient way to secure data while maintaining its usability for specific applications. Here are a few real-world use cases where polymorphic encryption proves particularly beneficial:
Customer Data Analysis in Retail
In the retail industry, businesses often need to analyze customer data to tailor marketing strategies and improve service. For example, a company might want to analyze purchasing patterns based on customer demographics, such as age or location.
With polymorphic encryption and polymorphic tokenization, the full customer profile remains encrypted. Your analytics store maintains a representation of the original data in the form of tokens that can support most analytical operations like joins, groups, and counts. Additionally, you can still execute operations on partial data, such as age ranges or location codes, without exposing sensitive information.
Performing such analysis with homomorphic encryption would be slow due to the high computational demands. The process of computing on encrypted data would make real-time analysis impractical. Traditional tokenization would require detokenizing the data to perform meaningful analyses, which can expose sensitive information and increase the risk of data breaches.
ID Verification
In customer service, agents often need to verify identities using sensitive information, such as the last four digits of a Social Security Number (SSN).
Using polymorphic encryption a customer service agent (CSA) can request the last four digits of a customer’s SSN and confirm their identity in real-time without decrypting the entire list of customer SSNs. The CSA only processes the relevant part of the data while keeping the full SSNs encrypted, ensuring privacy and security.
Credit Check
Bankers frequently need to assess credit scores to approve loans. They need to know whether a credit score meets a specific threshold, but not the exact value. What’s important is being able to perform an assertion on the sensitive data, not necessarily having access to the original value.
Using Skyflow’s polymorphic encryption, the system processes the encrypted score and returns a simple “yes” or “no” response, thus protecting the full credit score while still providing necessary information for loan approval.
Final Thoughts
While methods like homomorphic encryption and tokenization are powerful, they are either impractical from a performance perspective or break your existing workflows for search, AI, and analytics.
Polymorphic encryption is the solution to this.
By enabling specific operations on encrypted data and adapting to varied use cases, Skyflow’s polymorphic engine ensures that sensitive information remains protected while still being functional and usable. If you want to learn more and receive a custom demo, please contact us.
