What is Fine-Grained Access Control for Sensitive Data?
Sensitive customer data is essential to nearly every business and is closely associated with a business's most valuable asset – customer trust. This makes it critically important to carefully manage access to this data.
Data that could be used to identify an individual – things like a customer’s name, email address, and date of birth – is more sensitive than general-purpose data. To protect sensitive data from misuse, it should be governed by fine-grained access controls that limit its use to authorized purposes.
In this post, we’ll discuss the basics of fine-grained access control, how it differs from coarse-grained access control, and what it takes to create a system that uses fine-grained access control to govern access to sensitive data.
What is Fine-Grained Access Control?
Fine-grained access control is a method for providing highly granular control over who can access certain data, and in which format. Because fine-grained access control provides more nuanced control over data access than generalized (or coarse-grained) access control, it is well-suited for managing access to sensitive data, such as PCI data or PII.
A rule implemented with fine-grained access control can be simple – consider the following examples:
- Restrict access to only the last four digits of a customer’s social security number (SSN) for identity verification.
- Limit which phone numbers customers or gig workers have access to, and for how long, preventing potential misuse.
Fine-grained access control can help avoid overly-broad access to data. For example:
- In a school with fine-grained access controls, instead of giving all teachers access to all student data, a teacher can only access their student’s records for the classes that the student has with them.
- In a medical clinic with fine-grained access controls, instead of giving all doctors access to all patient data, doctors can only see the data of their patients, not all patients who visit the clinic.
This approach to access control avoids broad access to sensitive data (known as “coarse-grained access control”) that can compromise your privacy posture and lead to data breaches.
Let’s take a closer look at the differences between these approaches to access control.
Fine-Grained Access Control vs. Coarse-Grained Access Control
To understand fine-grained access control, it’s helpful to first understand how it compares against its simplistic relative – coarse-grained access control.
Coarse-grained access control is relatively inflexible compared to fine-grained access control, providing all-or-nothing access to sensitive data. For example, a coarse-grained access control policy might grant access to a whole database or table.
On the other hand, fine-grained access control allows for much more specific and nuanced control over data access. So instead of granting access to a whole database or table, with fine-grained access control you can control access at the level of columns, rows, or even substrings within cells (with masking and redaction).
Instead of simply granting or denying access based on a user's membership in a particular group, fine-grained access control lets you specify exactly which users have access to which types of customer data, in which privacy-preserving format, and under what conditions (i.e., according to location or other user attributes).
As you can see from reviewing this table, there are a lot of advantages to using fine-grained access control.
And as we’ll show below, using an intuitive policy expression language can reduce the complexity of implementing and maintaining fine-grained access controls.
What’s Required to Create a Fine-Grained Access Controls
The first step to implementing fine-grained access control is knowing what types of sensitive data you want to govern with an extra layer of protection beyond what you use for less sensitive data.
For example, if you work for a healthtech company, do you just need to manage access to the 18 HIPAA identifiers, or do you need to go further to include other types of sensitive data, such as payments (PCI) data?
After identifying your sensitive data types, the next step is to define all scenarios where sensitive customer data should be accessed, for what purpose, and by whom. Using a life insurance company that handles SSNs as an example, you’d ask questions like:
- In which situations can we use customer SSNs?
- Will every employee need full access to SSNs, or are there situations where only the last four digits are needed?
- How can we protect SSNs by preventing them from being copied or used outside of authorized workflows?
- How can we ensure that end users of our app can only view, update, and delete their own records, and no one else’s?
To better understand this, let’s look at an example of how a life insurance company could approach fine-grained access control for SSNs.
Governing Access to Social Security Numbers for Life Insurance
For a life insurance company, SSNs are required in the underwriting process, so it makes sense for the underwriters to have access. But after the policy is in effect, does the customer support and billing department, or anyone else, need full access to that data?
No, they only need the last four digits of the SSN for customer verification. That means there’s no need to display – or even decrypt – a full SSN for anyone but an underwriter.
Instead, you can map the relevant user attributes, such as role, department, geography, assigned customer, etc., against sensitive data in your data governance tool.
That way, when a new employee starts in the customer support and billing department, they have the right level of sensitive data access – not too much, or too little – from day one.
You may be thinking, wait, that’s it? Simple enough. I can do that in one weekend!
Well, not so fast…
First, You Need to Find Sensitive Data
You need to determine where all the sensitive customer data is to ensure these types of sensitive data are properly protected. After all, how can you govern access if you don’t know where the data is?
After you have located all of your sensitive customer data, if it’s spread across ten different systems, you would have to configure data access for ten different systems. And, this complexity increases exponentially if the attributes you need to pull to support workflows, such as analytics, are from multiple sources.
For example, let’s say that your company has a range of applications that require PII – an HR app, a Talent app, ATS, CRM, Billing, and ML – and all of these applications send data downstream to your data warehouse to support analytics.
This gives you a truly daunting data workflow, where PII is present nearly everywhere, resulting in a problem known as sensitive data sprawl:
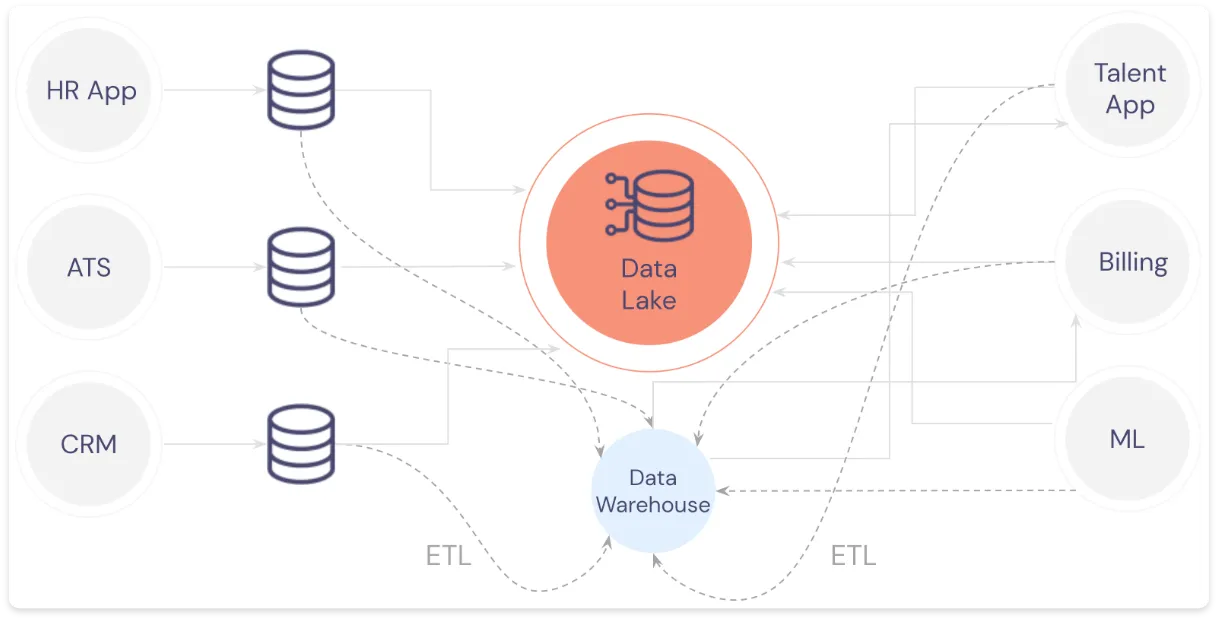
Oh, and what happens if you need to do one of the following?:
- Make changes because of a change in laws and regulations.
- Meet new data residency requirements in your existing market, or in a new market.
- Manage access to transient data that can’t be stored long term?
Ok, so maybe it’s not so easy.
Fine-Grained, Highly Flexible, Scalable Data Governance
Because customer trust is critically important to any business, it pays to put in the effort to govern sensitive customer data thoughtfully and effectively. Skyflow helps you do exactly that.
It’s much easier to protect sensitive data when you have fine-grained access controls that you can manage with an intuitive policy expression language. This is especially true when these policies are enforced in data-level CRUD operations, not in downstream systems that serve data to clients.
The best way to accomplish all of this is to isolate and protect sensitive data it as soon as it’s collected and stored in Skyflow Data Privacy Vault.
Isolate Sensitive Data, Centrally Manage it in Skyflow
With all of your company’s sensitive data elements – names, SSNs, etc – isolated in a vault, you can centrally manage sensitive data access by creating policies that use a combination of common attributes. These attributes can include roles and assignments, but they can also include never-before-available attributes like consent, IP address, and time from other systems to precisely define the sensitive data governance rules your business needs to both protect and use sensitive data.
You don’t have to settle for all-or-nothing access anymore. Instead, you can provide differential access to sensitive data for various roles based on business workflow needs. This lets you handle each type of sensitive data differently, so you can easily provide plaintext bank account numbers to money movement services but only the last four digits of account numbers and SSNs to customer support agents (CSAs).
Easily Configure Fine-Grained Access Controls with Skyflow
How easy is it to configure these types of fine-grained access controls? Skyflow’s intuitive policy expression makes what could be an onerous task as simple as possible.
Let’s take the example of granting CSAs read access to only the last four digits of customer SSNs. With Skyflow, you can set this access with an intuitive, easy to read policy like the following:
With a policy like this, even a compromised CSA client application won’t reveal full SSNs, because all but the last four digits of SSNs are redacted by Skyflow under this policy. This keeps full SSNs completely out of the CSA workflow.
Now, let’s say that you need to make this policy specific to residents of California. This could be complex if you’re using a less intuitive fine-grained access control system.
Fortunately, with Skyflow’s intuitive policy expression language, you just need to make one small change to the policy shown above, giving you the following:
The ease of maintaining and updating this policy makes access control both simpler to manage, and more effective.
If you compare redacting SSNs at query time to the traditional approach of sending full SSNs to a client application before redacting them in the client’s GUI layer, you can see how Skyflow’s approach to fine-grained access control helps to enhance the privacy and security of sensitive data. Skyflow’s approach protects full SSNs, even if your CSA client application becomes compromised.
You can further enhance access control for SSNs and other sensitive user data by incorporating context based on conditional rules encapsulated during API authorization. For example, you can use context-aware authorization to let your users view, update, and delete their own records – and no one else's.
Try Skyflow
To learn more about how Skyflow can help you manage access to sensitive data, see our blog post on Skyflow and data governance.
And, if you’d like to learn more about Skyflow and how its governance engine combines the ease of coarse-grained access control and the effectiveness of fine-grained access control, give Skyflow a try.
