Skyflow’s Approach to Zero Trust
Skyflow is the world’s first data privacy vault delivered as an API. Here’s how zero trust informed our approach to authentication and authorization.
As custodians of our customer’s sensitive data, we have an immense responsibility to provide exceptional data security. So when we started building Skyflow, we asked ourselves a very simple question with a much more involved answer: what does exceptional data security look like?
We resonated with the concept of a zero trust approach, where the default posture of an information system should be to “Never Trust, Always Verify”. If you would like a quick primer on Zero Trust architecture, check out this blog post. The zero trust approach goes beyond network security — it always assumes that the network has been breached and designs for data security as if there is no perimeter. We decided to take the zero trust approach and apply it to all aspects of data security. In this blog post, we will delve deeper into what Authentication and Authorization systems need to consider when designing for zero trust.
With each data access request, the goal for zero trust authentication and authorization is to answer the following questions:
.png)
Authentication
It all starts with authentication, which is the act of verifying that clients are who they say they are. Authentication applies to both human users that engage with the user interface as well as machine identities, which tend to be API clients.
Secure User Authentication
Secure user authentication requires a combination of multifactor authentication (MFA), identity provider (IDP) integration, and secure API authentication.
Multi-Factor Authentication (MFA)
Using a username and password is not secure given the sophisticated nature of today’s threat vectors.
MFA is an adaptive authentication technique where you use two or more factors in addition to your username and password (something you know) to verify who you are. These factors tend to be something you possess (your phone, FIDO2 keys) or biometrics (such as fingerprints or facial recognition). Current best practices recommend using an authenticator app or a FIDO2 security key as the second factor to securely authenticate the end user.
A password, which is something you know, can be compromised; but an app on your phone or a hardware key, which is something you possess, is much more difficult to compromise. Skyflow ensures all users go through an MFA flow before they are logged into their data vault.
Identity Provider (IDP) Integration
A typical modern organization uses about 80 different SaaS applications, creating challenges with respect to user onboarding and off-boarding. Additionally, not centralizing user credentials makes it very difficult to disable a user with compromised credentials across your network of applications.
We recommend leveraging an identity provider solution to centralize authentication. Integrating with an IDP using protocols such as SAML 2.0, OpenID Connect, and SCIM 2.0 enables automated user provisioning and logins. This integration also lets you customize the exact authentication schemes used so you can meet or exceed your organization’s security and compliance policies.
Secure API Authentication
Many software services use API keys or the OAuth2 client credentials grant type to authenticate API clients. Modes of API authentication that use static credentials have well-known gaps and can be easily exploited by man-in-the-middle attacks.
Skyflow leverages cryptographically-signed JSON Web Tokens (JWTs) for API authentication in accordance with the IETF OAuth2 JWT profile for client authentication specification. Customers need to sign JWTs with private keys which are known only to them to authenticate API clients in Skyflow. Private keys can be stored in encryption key vaults and can be dynamically invoked at the time of signing the JWT. With this mechanism, the private keys are never shared, thus keeping your API integrations secure.
Authorization
After you have asserted who you are, authorization determines what you can do. In the following section, we’ll take a closer look at how Skyflow’s authorization model helps you make dynamic, fine-grained zero trust policy decisions.
Policy-Based Access Control Model
Pure Role-Based Access Control (RBAC) systems are easy to use but have gaps because of their static nature. Attribute-Based Access Control (ABAC) systems are more sophisticated but can quickly become difficult to manage because of their complexity. Skyflow takes the best of both these models with a hybrid approach — Policy-Based Access Control (PBAC). With PBAC, granular policies that take resource attributes into consideration are authored and then attached to a role. This role is then assigned to a user or a service account to enforce fine-grained access control.
Dynamic Policy Enforcement
Authored policies and any changes to existing policies are dynamically pushed to the policy engine through an event-driven mechanism. The policy engine runs as an independent service within your vault’s infrastructure and caches policies locally. It acts as the policy decision point where the various parameters that are required to make a policy decision are evaluated for each and every incoming request according to the principle of "never trust, always verify". Because the policy engine is deployed in the same infrastructure as your vault and has caching and event-driven mechanisms in place, policies can be authored and enforced near real-time with very little latency.
Fine-grained Access Control for Data Minimization
Enforcing principles of least privilege is an effective way to reduce your attack surface area according to the zero trust approach. Additionally, this is a key mandate of the GDPR law: User accounts and apps should only have access to the specific fields that they need to perform a legitimate business function.
Data in Skyflow vaults is organized in a relational database with tables, columns, and rows. Using table-level, column-level, and row-level access control (along with support for SQL WHERE clauses) Skyflow enforces very granular and condition-based data access control policies:
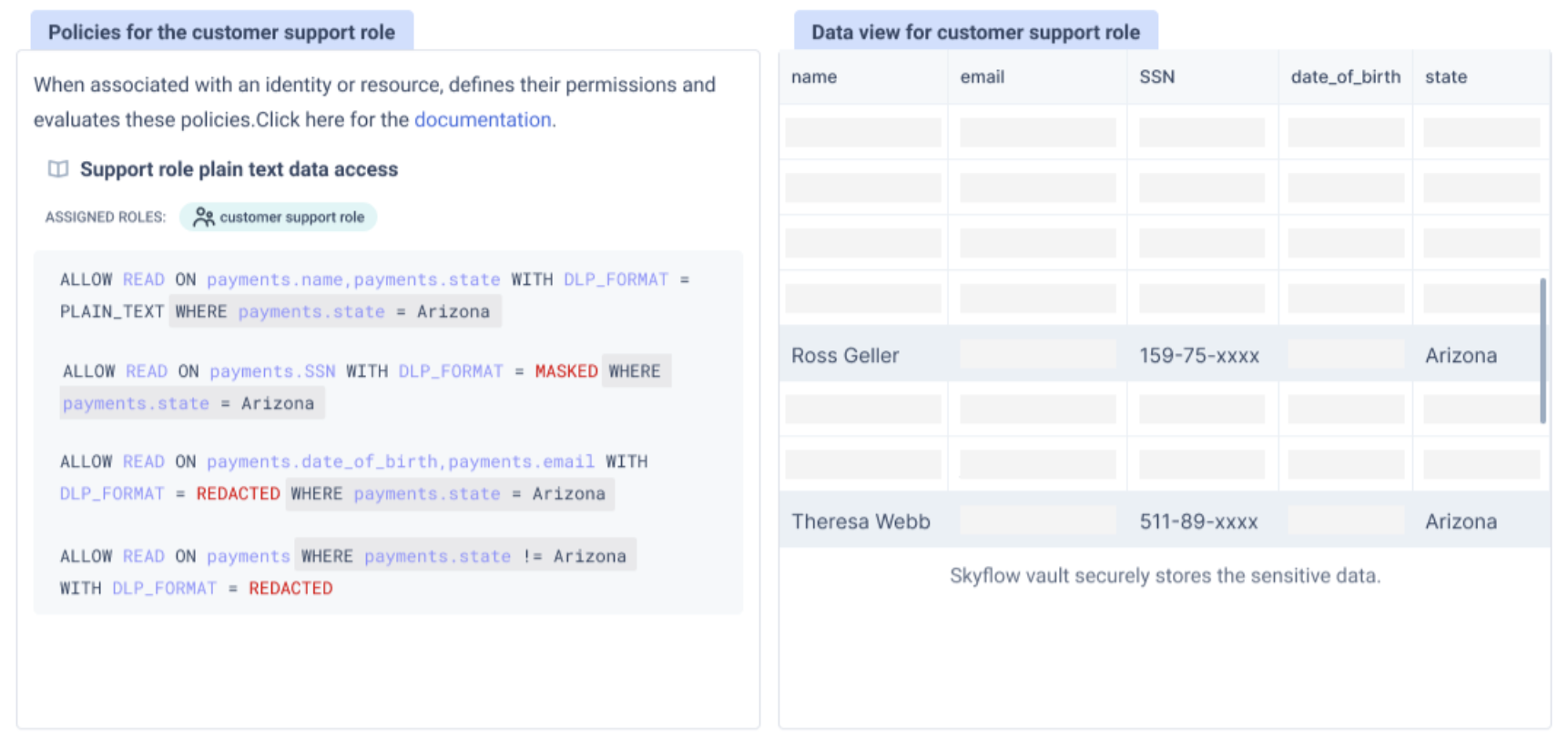
Privacy-Preserving Data Governance
Privacy preservation is one of the key value propositions of Skyflow. Skyflow employs techniques such as tokenization, redaction, masking, and encrypted operations to preserve data privacy.
To reinforce zero trust and the principle of least privilege on reading data, Skyflow’s governance engine can ensure that the same data is shared differentially based on the identity of the end consumer and their specific business use case. You can use the policy engine to author READ policies where certain actors get to read the data in plain text, while others can read a redacted or masked version of the data. For example, you may want to enforce a policy where a customer support agent may need to view only the last 4 digits of a consumer’s social security number (SSN) for identity verification purposes.
Continuous Access and Intent Evaluation
Most authorization systems keep a session active using long-lived access tokens. These access tokens may have been granted under a specific set of conditions that may change. A zero trust authorization system should re-evaluate if the user still complies with those conditions when making a decision on whether to continue allowing access to the data.
Additionally, intent-based evaluation ensures the continuous monitoring of API calls and the number of records requested per unit of time for any anomaly detection. Skyflow provides out-of-the-box policies to enforce zero trust for each and every data access request.
API Authorization
Service Accounts
Many other software vendors that use user-delegated OAuth clients are restricted to using coarse-grained permission schemes such as OAuth scopes, which act against the principles of data minimization. For example, scopes such as ‘read’ or ‘manage’ for a specific API endpoint are not granular enough to specify permissions at a table, column, or row level. Skyflow leverages service accounts to represent machine identities for API clients. A significant advantage of using service accounts is that customers can assign the same granular, fine-grained policies that are enforced for users to service accounts as well, thereby reducing the attack surface area.
Start Your Zero Trust Journey with Skyflow
In conclusion, building a zero trust data vault is a fairly complex process with many intricacies. When you embark on your zero trust journey you will need to leverage a system that makes use of many if not all of the aforementioned security features.
Skyflow Data Privacy Vaults provides exceptional data security when storing your sensitive data. By using our zero trust data privacy vaults, your teams can avoid the time and hassle of building all of these features from scratch, which reduces your time-to-market.
If you would like to see Skyflow in action, please contact us for a demo.
