Data Breaches: The Problem is PII
Companies like Affirm, Mercury, Stripe, Marqeta and so many other startups and even larger companies like Mastercard are now dealing with the mess created by the Evolve Bank data breach. Just a few weeks ago 150+ companies were dealing with the breach of their Snowflake data.
All these companies have amazing engineers, and often buy and use the best security products with a long list of compliance certifications. In fact, cybersecurity as an industry is making 100s of billions of dollars.
But why do we keep getting these data breaches that includes our SSNs, card numbers, DOBs, and so much more?
The root cause is a fragmented approach to data security. Simply buying more tools won't fix the problem. We need to rethink how we build our data infrastructure - and what it even means to secure our customers’ data.
The Problem is PII
Data breaches are a serious threat for any organization that handles sensitive customer information, but in industries like fintech and healthcare, the stakes are even higher. Hackers often target these companies because they have access to a massive amount of personally identifiable information (PII) like names, birthdates, and medical records.
The amount of data companies are holding onto is only getting bigger, compounding the problem, and making it even more difficult.
Protecting PII is hard. There are several key risks and challenges that make securing PII data difficult while also keeping it usable.
Understand the true risk of PII exposure – get the whitepaper →
Where is the PII?
Many organizations struggle to even know what PII data they have and where it resides. According to the Institute of Directors (IoD) and Barclays, over 40% of businesses don’t know where their critical data is.
PII can be scattered across multiple systems, databases, and cloud services, making it hard to get a comprehensive view. This makes the footprint for where PII could be really big. Without visibility into your PII landscape, it's impossible to properly secure and govern access to this sensitive data.
PII data gets duplicated and spread throughout an organization - the problem of PII sprawl. Point solutions are bolted onto each node within the growing graph of interconnected services, but each copy represents another potential vulnerability that needs to be secured and monitored.
Who has access to PII?
Both malicious insiders and external cybercriminals pose serious threats to PII data. Insiders with legitimate access can misuse or accidentally expose sensitive customer information. And sophisticated hackers are constantly looking for vulnerabilities to exploit and steal PII. Comprehensive access controls, monitoring, and threat detection are essential.
Data privacy regulations like GDPR, CCPA, and HIPAA are becoming more stringent and complex. Keeping up with the evolving compliance landscape, understanding how regulations apply to your business, and demonstrating adherence can be daunting.
Gen AI means more data and more risk
As businesses rush to adopt Gen AI technology, the above issues only get more complex. It’s difficult enough to navigate the maze of changing privacy regulations, but when you blend your customer data into an AI model, you have lost all control over who sees what, when, and where. You can’t delete it, you can’t definitively find it, and you can’t control access.
Isolate, Protect, and Govern PII
While we keep seeing breaches unfold, some leading tech companies like Apple, Google, Netflix, and a handful of others with the most PII have moved to a radically different architecture.
They invert the problem — you may have heard of zero-trust architecture — the general principle that you assume everyone is untrusted till proven otherwise and therefore every user, every app, every API has only the privileges and access that they need.
When you apply zero-trust principles to PII, you end up with a data privacy vault.
They isolate the PII separate from their existing systems, where they protect it, and control access. This effectively de-risks their existing application and analytical systems from potentially leaking PII because the PII doesn’t exist in any of those layers.
This architectural pattern, known as a data privacy vault (shown below), is also recommended as the future of privacy engineering by the IEEE.

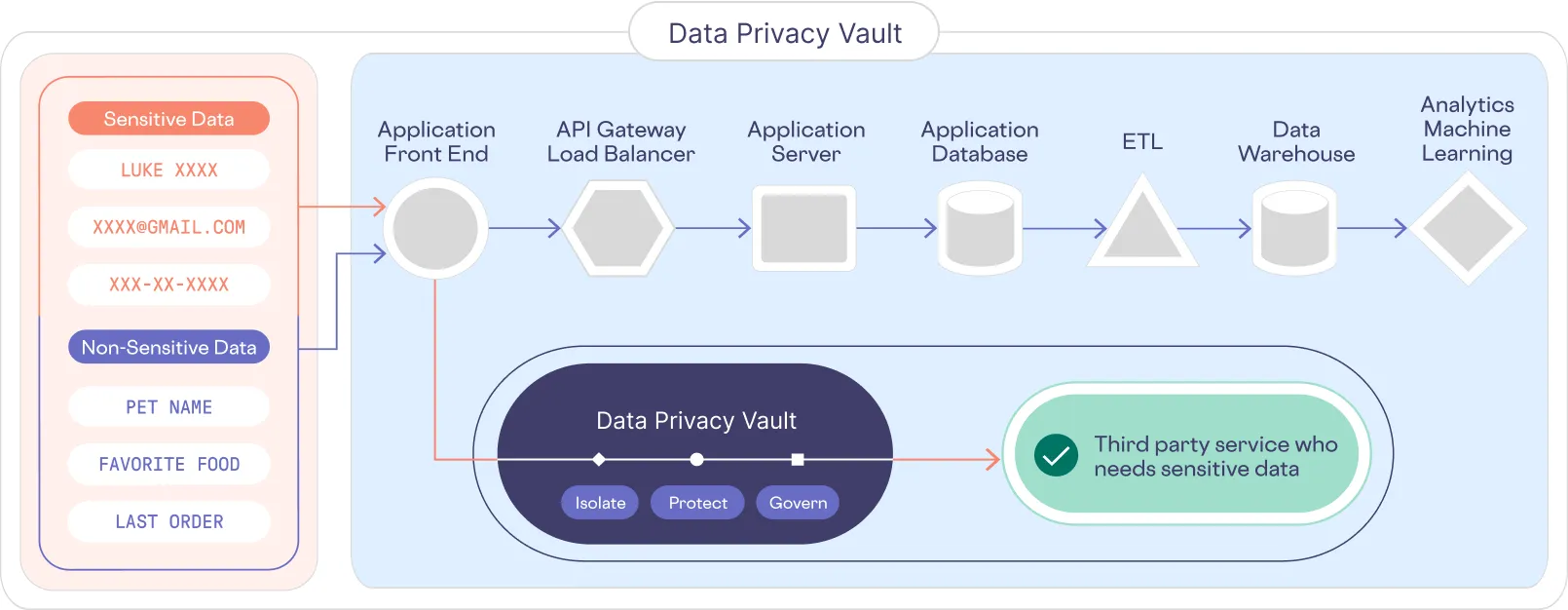
It’s all about reducing your surface area for attack because a breach is not really a breach if there is no PII.
We built a PII data privacy vault for everyone else.
At Skyflow we’ve taken this best in class approach to PII data protection and made it available as a service that you can run in our cloud or yours.
Here’s one of our customers with a lot of sensitive data - PII and PHI - GoodRx’s CTO, Nitin Shingate, speaking about how they use Skyflow in this fireside chat.

