Encryption Key Management and its Role in Modern Data Privacy
When managing your company’s most sensitive data, encryption is a must. To fit your overall data protection strategy, you need a wide range of options for managing your encryption keys so you can generate, store, and rotate them as needed.
If you’re responsible for sensitive data at your business, you know that it’s important to have choices when it comes to encryption key management. You might already have a data protection strategy that involves bring-your-own-key (BYOK) or integrating with a cloud-native key management service. Or, you might prefer to offload key management entirely. Either way, any new service that you’d consider using in your data architecture needs to support the strategy you have in place.
For businesses that handle sensitive customer data, there’s increasing regulation over how that data should be handled and secured from unauthorized access. In the EU, the General Data Protection Regulation (GDPR) recognizes encryption as “the best way to protect data during transfer and one way to secure stored personal data. It also reduces the risk of abuse within a company, as access is limited only to authorized people with the right key.”
The risk of sensitive data being misused or stolen can be limited, as long as just the people (and services) who are authorized to access data for approved purposes can access the key. Without proper management of encryption keys robust encryption techniques can be rendered ineffective. So, while encryption is a core feature of any effective data privacy solution, encryption only enhances data privacy when paired with effective key management.
In this post, we’ll take a look at the features of effective key management systems and discuss how Skyflow Data Privacy Vault can manage encryption keys for you with Skyflow Key Management, or integrate with an existing strategy built around AWS KMS or a BYOK approach.
Fundamentals of Encryption
Before discussing the ins and outs of managing encryption keys, let's first review the fundamentals of encryption by defining a few “key” terms:
- An encryption key is a piece of information (generally an integer, or a string of numbers and letters) that’s used with a cryptographic algorithm to encrypt or decrypt data.
- Encryption is the process of transforming data from a readable format (plain text), into an unreadable format (cipher text), to prevent unauthorized access. The encryption process requires a cryptographic algorithm and an encryption key.
- Decryption is the process of reversing encryption, and it requires access to the encryption key used when the data was originally encrypted.
One helpful analogy is to think of an encryption key as the digital equivalent of the combination used to open a lockbox or bank vault. Just as the combination to a lockbox gives you access to all of the contents of that lockbox, having an encryption key potentially gives you access to all data encrypted with that key.
The most important factors to evaluate how secure the contents of a lockbox are include the strength of the lockbox and the confidentiality of the combination. Similarly, the most important factors for determining the security of encrypted data are the strength of the cryptographic algorithm and the confidentiality of the encryption key.
The following diagram summarizes these fundamental aspects of encryption:
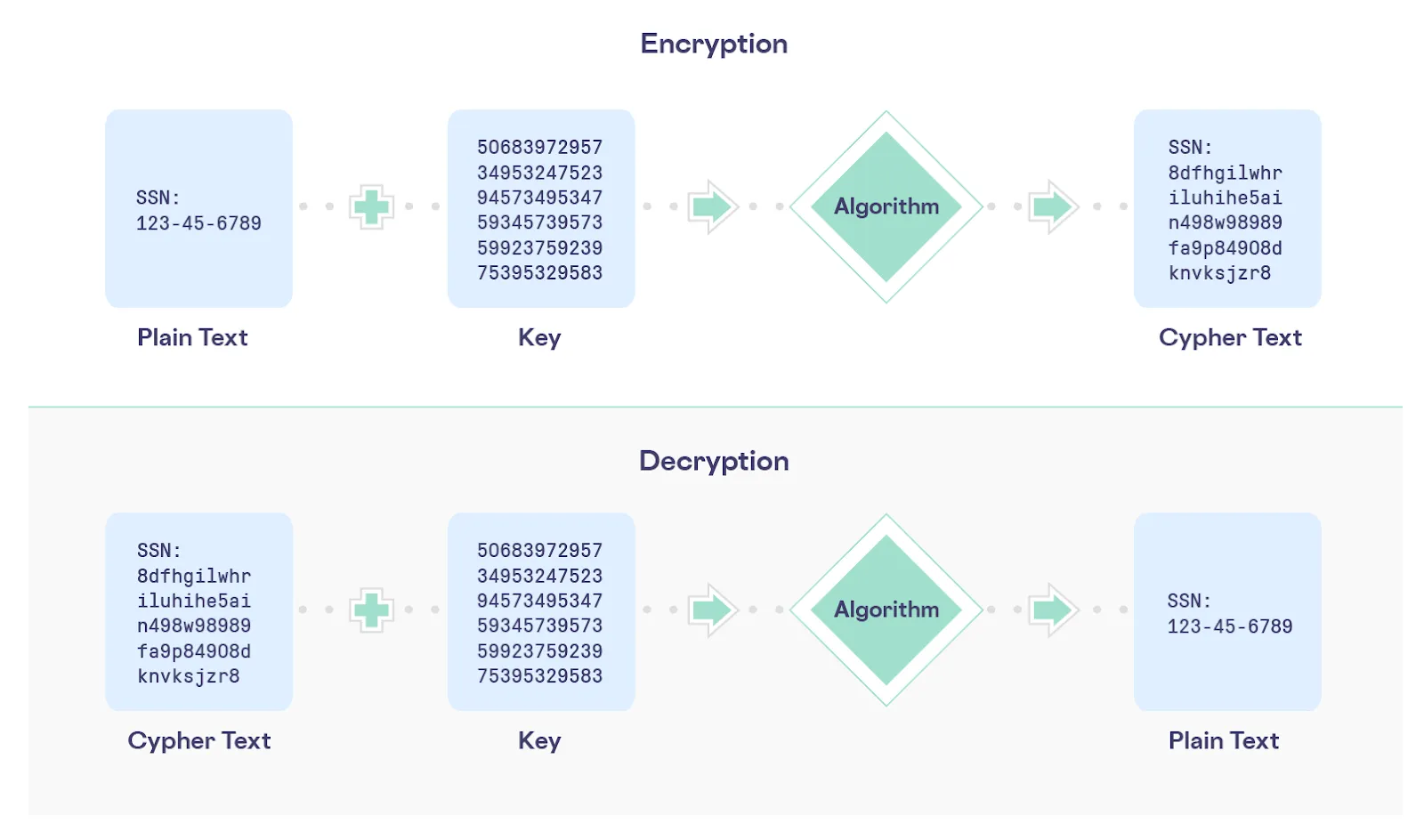
It’s also worth noting that you should combine encryption with other techniques like isolation, tokenization, and data governance to ensure the privacy and security of the most sensitive data that you handle.
Now that we’ve reviewed the basics of encryption, let’s zoom in on key management.
What Makes a Key Management System Effective?
An effective key management system needs to support the operations shown below, encompassing all of the stages of a key management lifecycle:

Each step in this lifecycle has specific requirements and considerations, which are discussed below:
- Generate: Cryptography generally uses integers for keys, although sometimes strings that consist of numbers and letters are used. You can randomly generate integers for use as encryption keys using a random number generator or pseudorandom number generator. It’s important to use a sufficiently long key length, because longer keys take exponentially longer to crack and you want to protect your encryption keys from brute force attacks which try every possible key.
- Register: An encryption key on its own is not very useful. To be useful, a key must be registered or linked within a system that tracks the relationship between the key and the data it protects so that the key can be found when there’s a need to decrypt and access data for authorized uses.
- Store: A key must be stored for future use. Key stores must be protected and limit access only to processes with an authorized use for specific keys.
- Use: After an encryption key is stored, it’s operational, meaning that it can be used to encrypt or decrypt data. Once operational, a KMS determines which operations to perform with a given key. Common security practices dictate that an effective KMS restricts the use of a single key to only one purpose.
- Rotate: Extensive reuse of keys can increase the attack “surface area” in the event a key is cracked by a brute force attack or other means. As time progresses, the amount of data protected by a key increases and so does the value of that key for a potential attacker. To mitigate some of this risk, common security practices recommend that an effective KMS periodically regenerates, or “rotates”, keys.
- Destruct: When a key has served its intended purpose it must be disposed of including potential redundancies like backups. Proving that a key has been deleted can be a requirement for compliance reasons. After a key is destroyed, any data encrypted by that key must be rendered inaccessible.
- Recover: An effective KMS needs a mechanism to provide a secondary means of access, such as backup, archival storage, or deletion reversal. Key recovery guarantees are typically time bounded, so recovery is only possible for a limited time after keys are deleted.
Now that we’ve looked at what’s required to create an effective KMS, let’s look at how Skyflow uses encryption keys and a KMS with Skyflow Data Privacy Vault.
Skyflow’s Granular Approach to Encryption Keys
Skyflow Data Privacy Vault is a best-of-breed solution designed to isolate, secure, and tightly control access to manage, monitor, and use sensitive data. If your organization handles sensitive customer data, including healthcare data (PHI), payment card data (PCI), or other personally identifiable information (PII) about your customers, Skyflow can help you protect this data without sacrificing data usability.
Skyflow uses a granular approach to encryption keys that includes a high-level master key called a Key Encryption Key (KEK) and lower-level Data Encryption Keys (DEKs). Regardless of whether you use Skyflow Key Management, AWS KMS, or a BYOK approach to manage each vault’s KEK, Skyflow will still use DEKs to encrypt data stored within the vault.
Data stored in Skyflow Vaults remains encrypted at all times. The KEK is used at a per-vault level to encrypt the DEKs, and the DEKs encrypt the data stored within the vault. This design provides data isolation and makes Key Management APIs independent across vaults. The use of multiple DEKs per vault help to enable Skyflow’s Polymorphic Encryption Engine.
Skyflow ensures your KEK and DEKs are available to decrypt data across different geographic regions, unless you restrict the availability of data to specific geographic regions to comply with specific data residency requirements. This is part of Skyflow disaster recovery architecture that ensures the availability of vault data in the event of a regional infrastructure failure.
How Does Skyflow Key Management Simplify Data Protection?
Skyflow Data Privacy Vault includes a built-in KMS that has all of the functionality described above, available using Skyflow’s Key Management APIs. These APIs leverage Skyflow's Role Based Access Control (RBAC) model, as follows:
- The Key Manager role is assigned to specific users or service accounts to restrict who is authorized to create and import keys to a given account.
- The Vault Owner role is assigned to a user or service account who authorizes key operations such as rotating that vault’s KEK or fetching vault metadata.
This granular approach to API permissions enforces principles of least privilege while still providing granular control over your keys.
What’s the Best Key Management Solution for Me?
By default, Skyflow manages the KEK for your vault using a Skyflow Managed Key. With a Skyflow Managed Key, you get the full benefit of Skyflow’s KMS. Using a Skyflow Managed Key makes sense for any organization not already using AWS KMS or a BYOK approach, but it’s especially useful for organizations that can’t easily answer questions like the following:
- Who has access to modify the state of my master encryption key?
- What data is encrypted by which encryption keys?
- When was the last time our encryption keys were rotated?
- In which cloud regions can our data be accessed?
If your organization already has a data protection strategy, Skyflow Vault can support it. Maybe you need to have control over your master encryption keys so you can “lock” the data in your vault so that nobody can access it, including Skyflow. Or maybe you’ve already centralized your management of enterprise master keys in AWS KMS.
If you don’t want to use a Skyflow Managed Key, Skyflow can support either of these scenarios:
- Manage Master Encryption Keys with BYOK: You can bring your own key material to Skyflow in a cloud-agnostic way. By using this option, you have the ability to manage the key in a secure environment such as a Cloud HSM and only Skyflow is able to decrypt and use your key.
- Manage Master Encryption Keys with AWS KMS: You can connect Skyflow to AWS KMS, which provides an effective key management system similar to Skyflow Key Management, but allows you to retain ownership of the key in your AWS KMS.
To learn more about Skyflow’s Key Management System, see the Skyflow Key Management Docs.
Give Skyflow a Try
Encryption key management is critically important to any company that handles sensitive data. You should carefully consider how best to manage your keys, whether you already have a data protection strategy built around AWS KMS or a BYOK approach or whether you’re defining your data protection strategy for the first time.
To learn more about how Skyflow Data Privacy Vault can help you to protect sensitive data, give Skyflow a try.
