How to Protect PII: Using Boomi and Skyflow to Automate Compliance
As organizations grow and connect more systems, managing sensitive data like Personally Identifiable Information (PII) becomes increasingly complex. Traditional approaches often lead to PII being scattered across various backend systems, creating compliance risks and operational challenges. The spread of PII not only increases the risk of data breaches but also complicates data residency and governance, making it difficult to ensure compliance across regions.
But what if there’s a way to protect your backend systems from PII, automate compliance, and simplify data residency?
By integrating Boomi with Skyflow Data Privacy Vault, businesses can reduce their compliance burden, and enhance security—all while keeping backend systems de-scoped from PII and residency concerns.
In this post, we’ll explore the limitations of traditional PII handling and how combining an integration platform like Boomi with Skyflow can reduce these risks.
Traditional PII Handling
In a typical integration scenario, PII is transmitted between various services, databases, and applications. Each system that touches the data often stores a copy of it—whether temporarily or permanently.
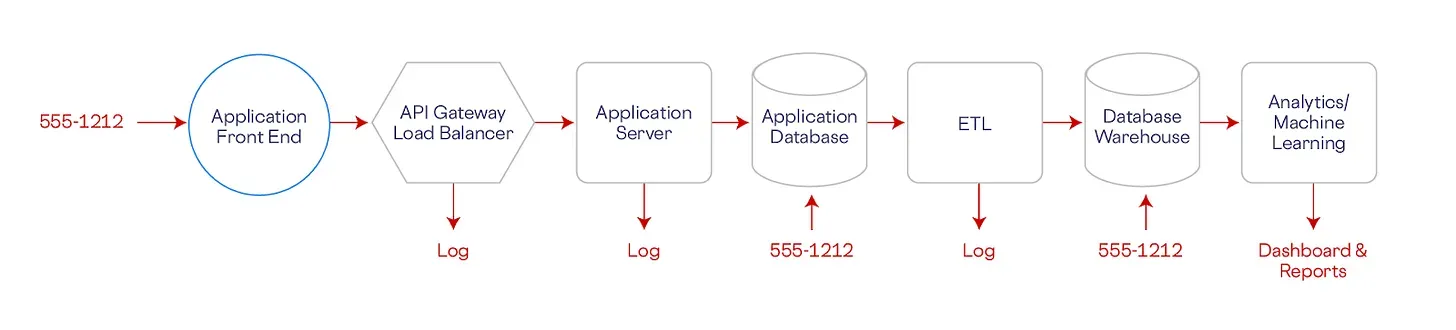
Over time, this leads to PII being scattered across multiple backend systems, creating several critical challenges:
- Increased Risk of Data Breaches: Every additional location where PII is stored becomes a potential point of vulnerability. If even one system is compromised, it can lead to a significant data breach, exposing sensitive information and harming your organization’s reputation.
- Complex Compliance Management: Compliance with regulations like GDPR, CCPA, and HIPAA requires strict control over where PII is stored and how it is accessed. When PII is dispersed across numerous systems, it becomes difficult to track and manage, increasing the likelihood of compliance failures.
- Data Residency Challenges: As organizations expand globally, they must comply with varying data residency requirements, which dictate where PII can be stored and processed. When PII is scattered across systems in different regions, ensuring compliance with these requirements becomes a logistical nightmare. The more places PII resides, the harder it is to ensure it remains within the appropriate jurisdiction, putting the organization at risk of non-compliance.
Integration platforms like Boomi play a crucial role in streamlining data management by centralizing the routing, transformation, and integration of data across various systems. They help enforce consistent policies, manage traffic, and simplify the integration process. While API gateways manage data flow efficiently, they do not inherently prevent PII from being stored or processed in every system it touches, perpetuating the risks of data breaches and compliance failures.
Luckily there’s a solution to this problem originally pioneered by companies like Netflix, Google, Apple, and Goldman Sachs and now touted by the IEEE as the future of privacy engineering, the PII Data Privacy Vault.
How to Protect PII with a Data Privacy Vault
A data privacy vault isolates, protects, and governs access to sensitive customer information like PII, while still allowing that data to be used effectively.
With a vault architecture, you store sensitive data in your vault, isolated outside of your existing systems. Isolation helps ensure the integrity and security of sensitive data as well as simplifying regionalization of this data.
Skyflow uses opaque tokens that serve as references to sensitive data stored in traditional cloud storage and downstream services. A data privacy vault can store sensitive data in a specific geographic location and tightly control access to this data. Other systems only have access to non-sensitive tokenized data. This effectively removes sensitive data from your existing infrastructure, thereby reducing the compliance and security burden on your systems.
Consider an example where your application collects a phone number. In a vault-centric architecture, the phone number is sent directly to the vault from the frontend. This approach ensures that sensitive data is de-identified as early as possible in its lifecycle. The vault stores the actual phone number securely and generates a token—a de-identified reference— that is sent back to the frontend. This token has no direct mathematical link to the original data, making it impossible to reverse-engineer.
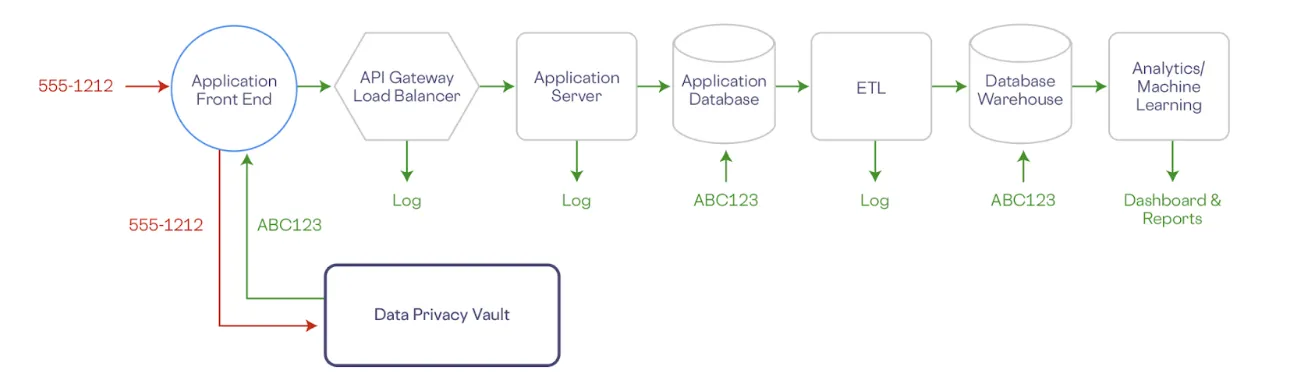
However, fully realizing these benefits requires more than just a vault. To keep PII out of your backend systems entirely, you need a comprehensive solution that integrates data privacy at every stage of the data flow. In the next section, we'll explore how combining Skyflow Data Privacy Vault with Boomi’s API gateway enables you to achieve this, ensuring that PII remains isolated, secure, and out of your backend systems.
Keeping PII Out of Your Backend Using Boomi with Skyflow
Imagine a simple web application running on AWS, with services like EC2 for compute, DynamoDB for database storage, and Redshift for analytics. In this setup, Boomi serves as the API gateway, managing all incoming and outgoing traffic between your users and backend services.
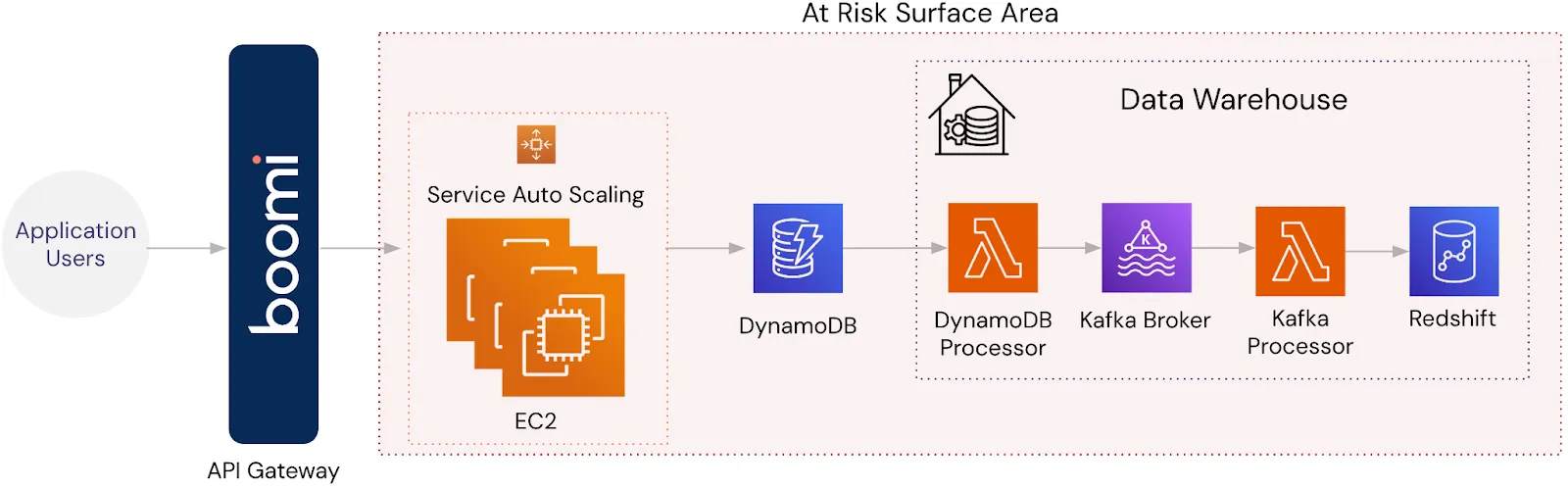
Traditionally, all data, including PII, flows through Boomi to downstream services like DynamoDB and Redshift. This means PII is stored, processed, and potentially analyzed across multiple systems, putting your entire backend infrastructure within the scope of compliance regulations. The more systems that handle PII, the greater the risk of a breach, and the more complex your compliance efforts become.
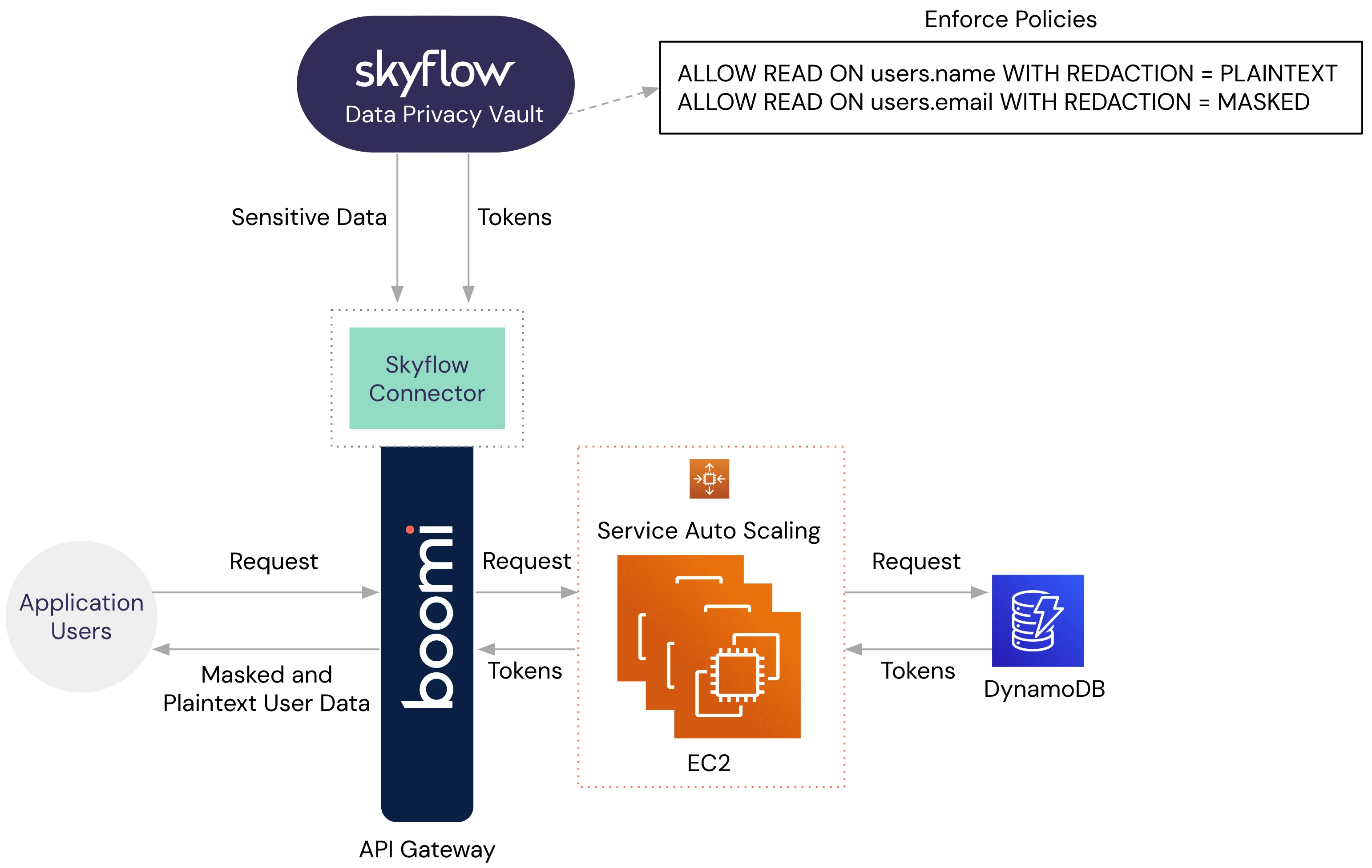
This is where the integration of Skyflow with Boomi can transform your data architecture. Boomi supports a native Skyflow connector, which makes it easy for any Boomi customer to use drag and drop features in Boomi platform to isolate, protect, and govern access to PII in their Skyflow vault.
With the Skyflow connector, you can automatically intercept PII as it passes through the API gateway. Instead of allowing PII to flow into your backend services, the sensitive data is securely transformed by your data privacy vault into non-sensitive tokens. These tokens are then passed to your backend systems, allowing them to function as needed without ever touching the original PII.
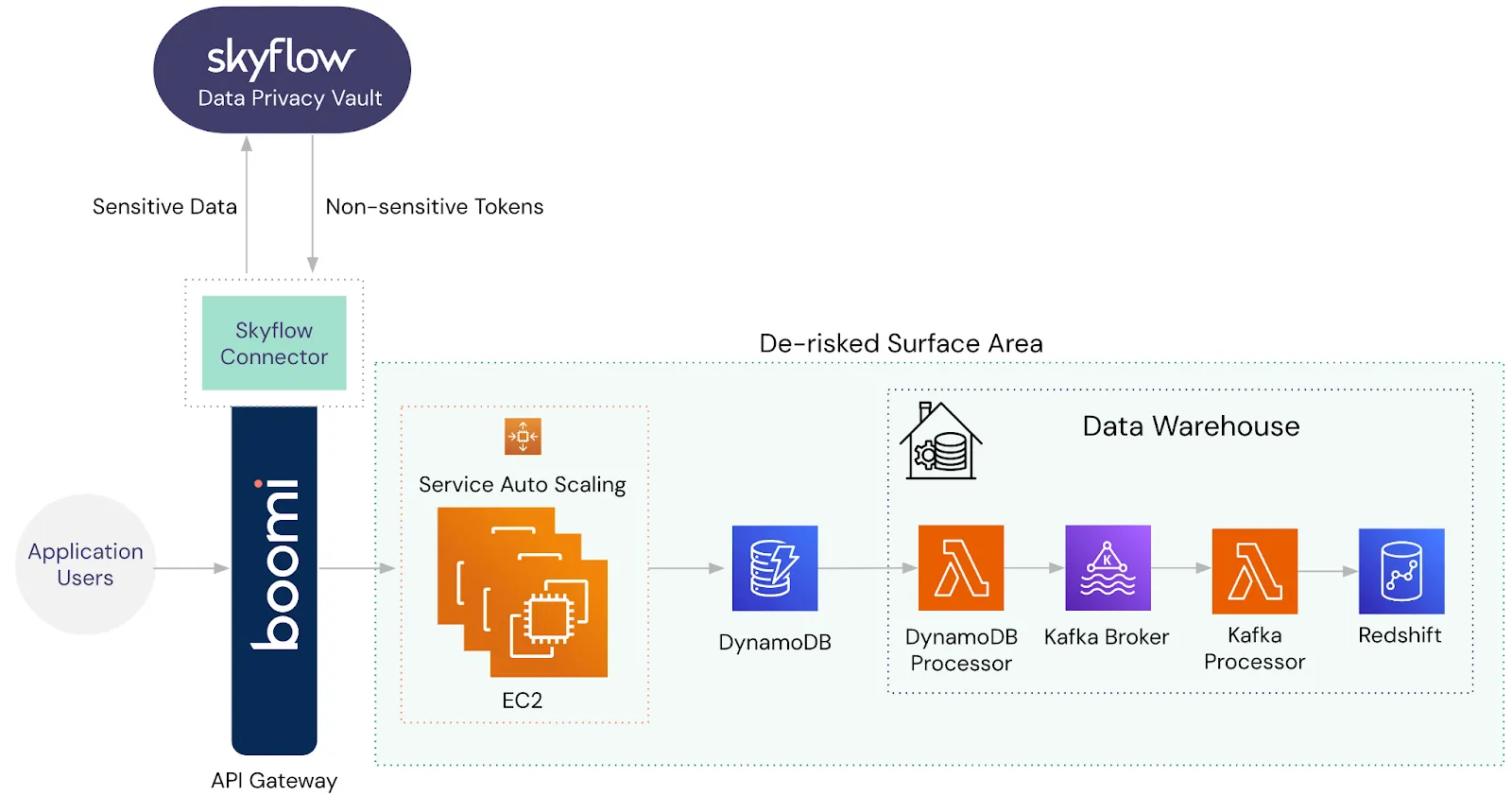
This approach not only protects PII but also effectively de-scopes your entire backend from compliance requirements related to data protection.
Retrieving and Re-identifying PII
At some point in the lifecycle of customer data, you’re going to need to re-identify PII. You can’t simply lock it up and throw away the key.
For example, we may need to reveal some of the data to a customer support agent, an IT administrator, a data analyst, or to the owner of the data. In this case, we want to re-identify it as late as possible, by taking advantage of the Boomi Skyflow connector.
We also want to limit what a user has access to based on the operations they need to perform with the data. While I might be able to see my full phone number, a customer support agent likely only needs the last four digits of my phone number and an analyst maybe only needs the area code for executing geo-based analytics.
The vault facilitates all of these use cases through a zero trust model where no one and no thing has access to data without explicit policies in place. The policies are built bottoms up, granting access to specific columns and rows of PII. This allows you to control who sees what, when, where, for how long, and in what format.
Let’s consider the situation where we have a user logging into our application and navigating to their account page. On the account page, we want to show the user their name, email, phone number, and home address based on the information they registered with us.
In the application database, we’ll have a table similar to the one shown below where the actual PII has been replaced by de-identified tokens.
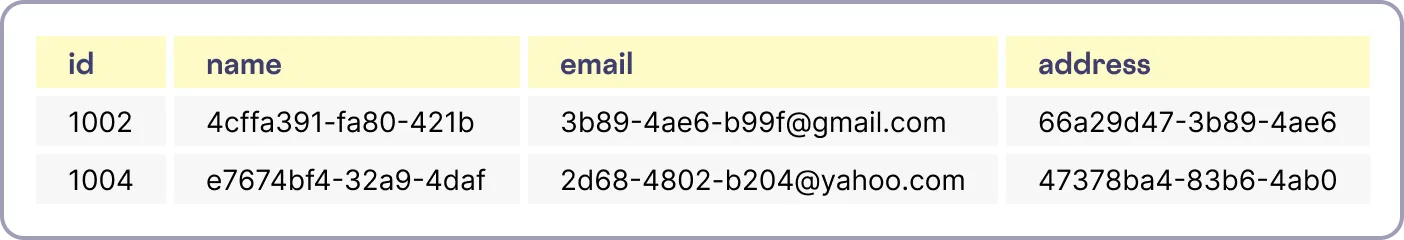
As in the non-vault world, the application will query the application database for the user record associated with the logged in user. The record will be passed to the Boomi API gateway, which will exchange the tokens for a representation of the original values depending on the policies in place. See the image below.
Bringing It All Together
Understanding how to protect PII is crucial. By integrating Skyflow and Boomi, you create a modern secure solution that effectively keeps PII out of your backend systems, significantly reducing compliance risks and the likelihood of data breaches. With Skyflow handling PII as a shared service, your backend services are no longer burdened with managing or securing sensitive data, allowing you to maintain both security and scalability.
Additionally, the vault architecture supports other use cases that involve sensitive data, like handling credit card information, data residency, and LLM privacy. You’re able to support all the workflows you want to perform with sensitive customer data while offloading the protection to your vault.
Finally, knowing how to protect PII using modern solutions like Skyflow for Boomi not only strengthens your security posture but also simplifies your architecture. This approach ensures your organization remains compliant while focusing on growth and innovation, free from the complexities of traditional PII management.
If you want to learn more, see details about the PII Data Privacy Vault or contact us for a demo.
